Cyber Risk Insurance Protection
Getting insurance—toolkit for customers
This section is designed to equip you with the right tools to talk about cyber coverage with your clients.
You and your team can take advantage of the materials to help your clients understand the potential impact on their businesses.
This section includes information on
- how to evaluate coverage and what to look for
- determining how much coverage is needed
- checklists to match risks and cyber coverage needs
- links to a variety of PIA Partnership cyber insurance programs
69% of agents said they are very concerned about the rising cyber threat facing their customers. Only about half of those surveyed agree clients are generally well prepared to prevent and/or limit the damage from cyberattacks or have enough coverage for such risks.
NU PropertyCasualty360
While 85% of agent/broker respondents said discussing cyber insurance options with clients is a high priority, businesses surveyed indicated that agents/brokers were rarely the first to initiate discussions about buying a stand-alone policy.
NU PropertyCasualty360
Your customers—especially those in the middle market—buy cyber insurance for a variety of reasons, and fear is a big part of that decision. This chart from a 2019 Deloitte study shows how those reasons stack up.
Fear often motivates the purchase of stand-alone cyber insurance
Reasons companies brought a stand-alone cyber insurance policy: 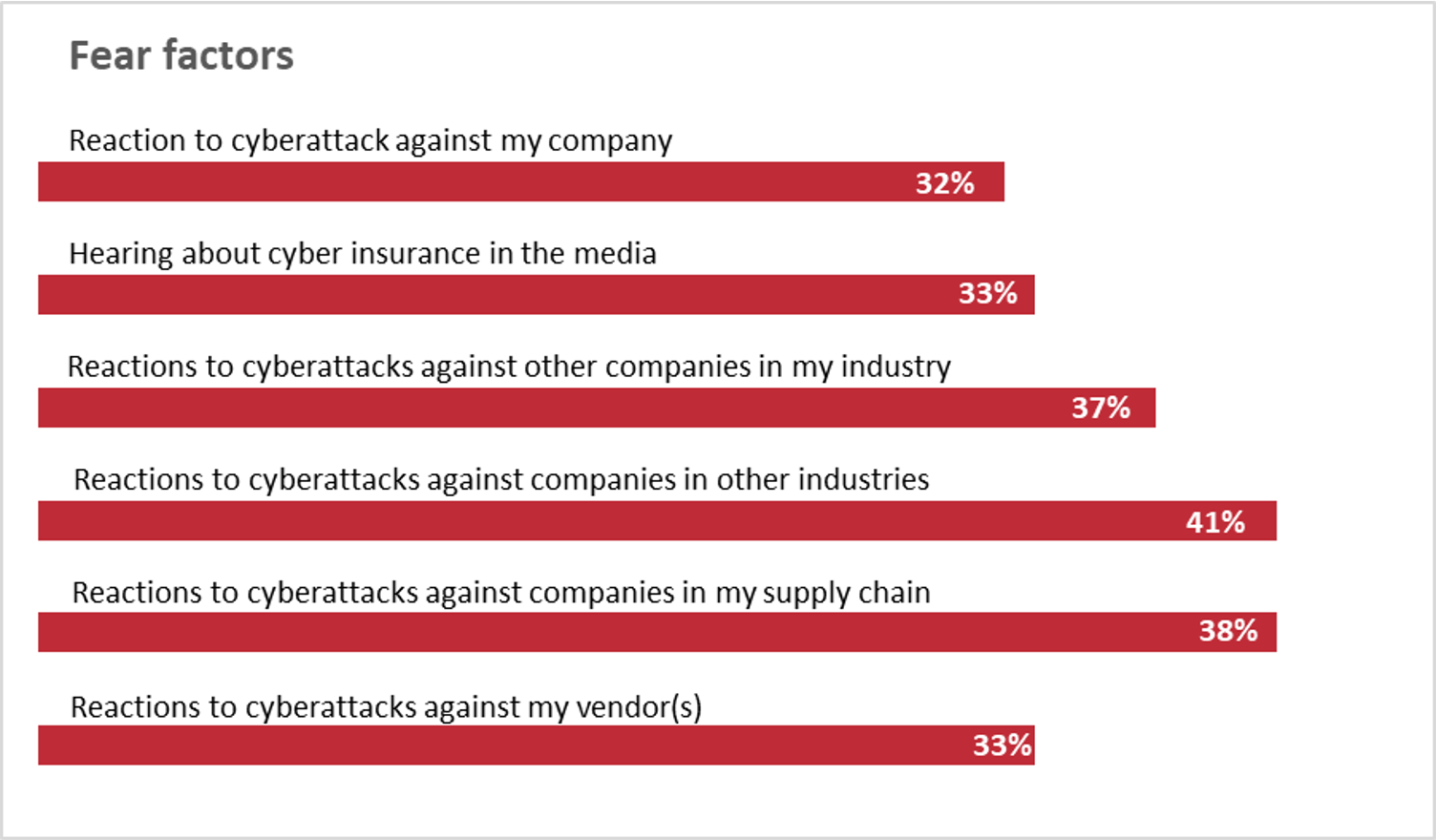
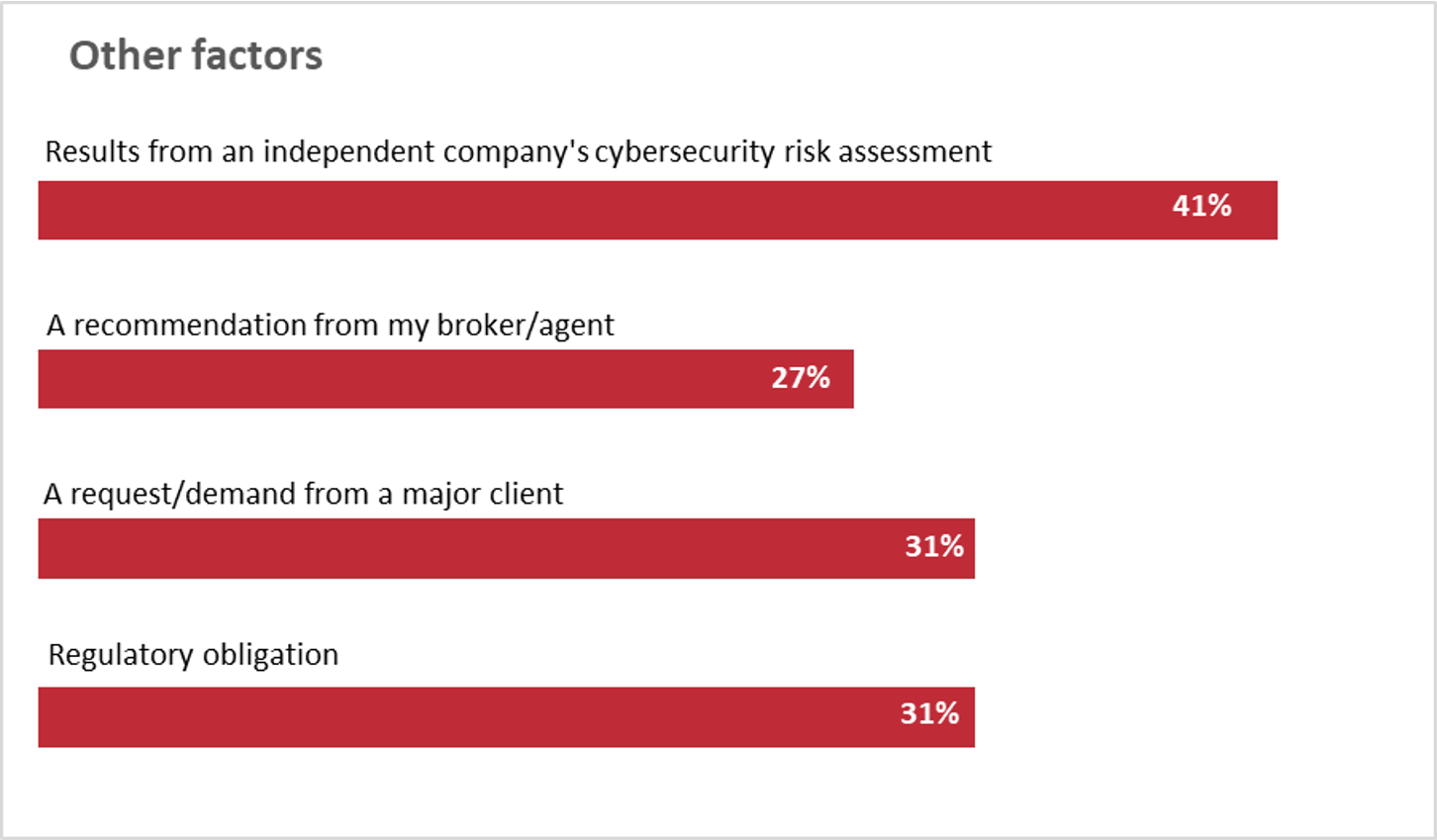 Source: Deloitte 2019 Middle Market Cyber Insurance Survey.
Source: Deloitte 2019 Middle Market Cyber Insurance Survey.
A cyberattack can put a small business out of business. Having the right insurance can help a company stay in business.
Understanding the 4 steps to a sale
- Does your company handle client financial or health information? (many businesses don’t always realize that they do)
- Do you host a public website that customers interact with?
- Do you have any types of online shopping facilities?
- Do you use a third-party vendor to manage your systems or network?
- Do you use third-party applications (in the cloud)?
- Do you enable your team members to bring their own devices?
- Have you ever been a target of ransomware or know someone who has been targeted?
- Do your existing insurance policies exclude or deny coverage for cyberattacks?
- What would the impact of a disruption to your business look like?
- Is having a good reputation in the community or market important to your business?
- Have you read your vendor contracts and do you understand the responsibility they are/aren’t taking when it comes to data security?
- Have you calculated the actual cost of a breach, including legal, customer notification, forensics, credit monitoring, PR and other?
- What is available from the insurance companies you represent? Insurance plans are not standardized and can vary widely. The space is also evolving, and insurance plans can change.
- Weigh the options, including access to experts.
- Understand the exclusions.
Insurance covers the loss of money resulting from a bank transferring funds based on fraudulent instructions received from someone pretending to be the authorized user.
Things to watch for:
- Policies typically cover the loss if—
- Instructions are initiated by phone, fax, email or online.
- Applies to money and securities, not property or data.
- May be contingent on the company following security protocols.
- Social Engineering Fraud is often not covered, but can be covered by a separate endorsement.
- Coverage may be a sub-limit of the policy limit.
- Funds transfer fraud may trigger other coverage under Data Breach or Network Security.
- Funds Transfer coverage can be found in a stand-alone Crime Policy or maybe a sub-limit as part of a BOP or Management Liability Policy.
- Some of the underwriting factors include: frequency of funds transfer activity, the dollar value of transfers, funds transfer controls, whether the company allows transfers per email instruction, how vendor changes are made, whether or not there is employee training and claims history.
Insurance covers the payment demanded in order to stop attacks on the company’s website, network, or computer systems.
Things to watch for:
- Coverage is usually triggered when a threat is received—either an attack on the computer system or release of confidential information.
- Something—usually money—is demanded from the company.
- Actual intrusion isn’t necessary—it’s about the threat.
- Ransomware coverage is found in cyber policies, but there's also coverage under kidnap ransom & extortion policies.
- Ransomware coverage may be coordinated with other parts of a cyber policy such as network security liability, data breach, data asset restoration or business interruption to address an actual data breach or system intrusion.
- Companies often work with agents/insurers to determine the best course of action.
- Agreement by the insurer to pay the ransom is usually a policy requirement.
- The insurer’s response team usually knows about the ransomware used.
- Coverage may be sub-limited.
- Demands are usually small so a low retention is helpful.
- Some of the notable exclusions include: acts by an insured (crimes), threats to third-party systems (such as utilities), amounts paid prior to notifying the insurer, amounts needed to improve systems following an attack.
- Some of the underwriting factors include whether the company has security controls, disaster recovery plans, data encryption, intrusion detection software, and claims history.
Insurance covers the direct loss from the impersonation of an employee, vendor, or client.
Things to watch for:
- Some policies require a verification procedure.
- Social Engineering endorsements can be found on some crime and cyber policies. It’s a newer coverage and not all carriers offer it at this time.
- Without this endorsement, there will likely be no coverage found in any policy. Direct loss from errors is not generally covered.
- Notable Coverage Features:
- Covers direct loss; excludes indirect or consequential damages. (For example, late fees owed to a vendor who didn’t receive payment.)
- Usually covers fraudulent instructions received by email, fax, phone, or in writing.
- Form may have a verification procedure requirement such as a callback.
- Coverage is usually sub-limited.
- Underwriting Factors:
- Frequency and amount of funds transfer activity
- Funds transfer controls
- Whether or not transfers per email instruction are permitted
- Verification of vendor changes
- Employee training
- Claims history
Insurance covers the loss of income and costs in excess of normal operating expenses required to maintain the business and restore operations. It may also cover dependent business interruption.
Things to watch for:
- Traditional BI Coverage is not sufficient. Property policies do not extend coverage to loss or damage to electronic data. Data is not considered a physical object subject to loss or damage.
- An incident usually triggers breach response coverage (forensics expenses, data restoration).
- System failures due to employee error are probably not covered.
- The BI sublimit caps the payout under the policy. Coverage will often include a separate BI deductible or BI waiting period, either in hours or days, before liability will arise under the policy.
- Key exclusions include system upgrades and utility failures.
- Some of the underwriting factors include the business size, industry control of the environment, the breach response plan, and claims history.
- Insurance typically pays for breach response and expertise.
Insurance covers expenses for breach response/expertise, response plan, IT security experts, legal fees, PR consultants, customer notifications/credit monitoring, contractual/statutory obligations, PCI fines/penalties, regulatory defense, data restoration and litigation.
Things to watch for:
- Policies vary in how they address limits. Common structures include (1) everything falls within one limit (shared) or (2) coverages fall under their own limit (separate).
- Common exclusions:
- Intentional acts
- Utility or infrastructure failure
- Unencrypted information
- Wrongful collection
- War and terrorism
- Rating Factors include class of business, revenue, payment card transactions, records stored, loss history and control environment.
Insurance covers the loss of damages and legal fees incurred as a result of unauthorized use or access to your systems, virus transmissions, and distributed denial of service attacks (DDoS).
Things to watch for:
- Policies typically cover the loss if—
- Unauthorized access to the Insured’s network or unauthorized use of the Insured’s network.
- The failure to provide an authorized user with access to the Insured’s network (DDoS).
- The transmission of a virus to a customer or other third-party system.
- A third party tricking a customer or business partner into releasing private information or transferring money by impersonating the Insured’s company or one of its employees.
- Coverage is contingent on a claim being made which can include a written demand for monetary damages or injunctive relief, a regulatory action, written request to participate in an alternative dispute resolution proceeding, or a civil or criminal proceeding.
- Coverage varies widely.
Insurance covers third-party damages and legal fees incurred as a result of a media wrongful act committed via the insured’s organization’s website or social networking account. Some policies may cover printed material, as well.
Things to watch for:
- Examples of wrongful media acts include: defamation, product or company disparagement, invasion of privacy, commercial appropriation of name, persona, voice or likeness, plagiarism, copyright infringement, trademark infringement, improper deep linking, false advertising (in some policies).
- Coverage varies widely.
- Common Exclusions
- SPAM
- Unlawful collection of data
- Discrimination
- Patent infringement
- False or incorrect advertising
- Insider ownership disputes
- Licensing fees
- Setting proper limits for your client is an important part of the equation.
- There's no set formula to use.
- You may want to start with the cost of a breach—estimated to be $141 per record or more. Using that model—
| # of breached records | direct costs |
| 1,000 | $141,000 |
| 10,000 | $1,410,000 |
| 100,000 | $14,100,000 |
| 1,000,000 | $141,000,000 |
This is just a starting point. Direct costs don't include defense and settlement or judgment costs.
This includes reviewing the insurer responses based not just on premium, but considering the coverage terms and conditions, limits and deductibles. Read the proposals to truly understand how the policies work and compare them to each other.
Overcoming barriers to a sale
Most companies mistakenly assume that cyber coverage is included in their current insurance policies. Agents need to educate them about the risks and the insurance available.
Common barriers:
This can be a tough sale—first time buyers are often confused about cyber products and how they work. This is where education about the risks, particularly effective use of case studies, can help. Hearing about cyber attacks and the consequences can be a big motivator in making the sale.
The numbers are scary. Cyber breaches are on the rise. Consider sharing these recent metrics about ransomware from Marsh.
148% increase in ransomware attacks fueled by the pandemic.
$154,108 was the average ransomware demand in Q4 2020.
21 days was the average downtime in Q4 2020.
70% of ransomware attacks in Q4 threatened to leak data.
It takes only 90 seconds for a new Remote Desktop Protocol (RDP) to be discovered once it hits the internet.
1 in 3,000 emails contains malware.
Cyber insurance for your clients
Cyber insurance for your agency
General cyber information for your clients and you
Top 7 Tips for Cyber Protection
Want to Test Your Cyber-Risk Knowledge? Test your cyber smarts now!
For Liberty Mutual Commercial Appointed Agents/Brokers only (login required):
Cyber Insurance for Business Owner’s Policy (BOP) - eCLIQ® Product Highlights
Cyber Insurance for Package and Monoline GL - eCLIQ® Product Highlights
If your clients' organizations experience a data breach, how prepared are they to respond? As a Liberty Mutual Insurance policyholder, they have access to the risk management tools on the eRisk Hub portal.
As a business owner, you may have learned the hard way that computer security and data breaches are not just a risk for giant multinationals or government agencies. Because we understand the risks associated with electronic devices and online data, Liberty Mutual offers data breach and cyber insurance, as part of a package or general liability policy. Learn more.
Data Compromise Plus® - package (all states)
Cyber information for Personal Lines
Hanover's home cyber protection aids with recovery and related expenses resulting from a cyberattack, data breach, online fraud, cyber extortion or cyberbullying event affecting members on a Hanover homeowner's policy.
This coverage applies to cell phones, tablets, and smart devices connected to the account. This includes, and is not limited to, wearables, thermostats, entertainment systems, home security devices, smart appliances and much more.
For more information:
- Cyber coverage for homeowners
- The answers to all your questions about cyber insurance for homeowners
- Video for keeping your home and phone safe from Cyber attacks
Cyber information for Commercial Lines
The Hanover's holistic suite of cyber solutions is designed to help protect your clients from losses related to data breaches and cyberattacks. We specialize in writing cyber coverage for business in the following industries:
- Construction
- Financial institutions
- Manufacturing
- Non-profit
- Professional services
- Retail
- Technology
- Wholesale
Underwriting Tip: Cyber risks are constantly changing – Help protect your policyholders with Cyber Suite!
In today’s world, cybercrime is everywhere. Data breaches and ransomware attacks at large corporations are often featured on social media and the news. However, small companies are even more vulnerable because they don’t have the budgets to invest in IT safeguards.
The price of cybercrime is high, and small businesses can’t afford it. According to a 2019 study by Zogby Analytics, nearly 40% of cybercrime victims spent $50,000 or more responding to the attack. That kind of money could damage or cripple a small business.
West Bend’s Cyber Suite is a comprehensive cyber insurance solution to help businesses respond to a variety of cyber incidents. These coverages can help your policyholders recover from an otherwise devastating cyberattack.
First Party Coverages Include:
• Data Compromise Response Expenses
• Computer Attack and Cyber Extortion
• Misdirected Payment Fraud
• Computer Fraud
Third Party Coverages Include:
• Data Compromise Liability
• Network Security Liability
• Electronic Media Liability
Identity Recovery
Annual Aggregate Limits Available*: $25,000 up to $5,000,000.
*Limits $500,000 and up are subject to underwriting approval.
You’ll find more information about the many benefits of Cyber Suite with our marketing pieces. These items are available on WBConnect:
• Cyber Suite Claims Scenarios/Limits
• Cyber Suite Coverage
• Cyber Suite Higher Limits Questionnaire
