Cyber Resources for Your Agency
- Security tips
- Employee training
- Password management
- Antivirus protection
- Business recovery plans
- Vendor management
- Security mindset
- Managed Local Security Services Provider
- Multi-factor authentication
- Emerging risks
Note that the PIA Partnership does not endorse or recommend any of the programs or vendors here. They are provided for informational purposes and agencies are encouraged to research and evaluate on their own.
Basic Toolkit
1. Security Tips
Train employees to update their software
- Keep your software up to date—both your operating system, and applications.
- Turn on automatic system updates for your devices.
- Make sure your desktop web browser uses automatic security updates.
- Keep your web browser plugins like Flash, Java, etc. updated.
Ways to make your cellphone more secure
97% of Americans own a cellphone, according to Pew Research
Phones contain significant information from contacts and addresses and phone numbers to being a place to save financial and credit card information and even passwords. Protecting them is very important.
- Lock your home screen and require a password or biometrics to unlock
- Don’t use public charging ports
- Don’t use public WiFi Update
- Update your phone’s software when prompted
- Keep Bluetooth and WiFi off when you’re not using it
- If you store passwords on your phone, put them in an encrypted file
- Consider using 2-factor authentication on your phone
- You can use your phone’s hotspot relatively safely but be sure to use a strong password to access and select WPA2 network security (versus WEP or WPA)
Additional resources:
The National Institute of Standards and Technology develops cybersecurity information and standards.
Checklist for working from home
- All employees should sign onto a virtual private network with strong end-to-end encryption.
- Secure all employee devices with anti-virus software.
- Have password policies in place for all employees-teach them how to have strong passwords.
- Use multi-factor authentication for all employees.
- Advise employees to turn off Siri, Alexa or other devises during video meetings and conference calls.
- Advise employees not to work from public places where they connect to public Wi-Fi or screens can be viewed.
- Devices should not be left in locked cars.
- Device encryption should be enabled
One of the most important steps you can take to ensure your agency’s security is to train your employees. This doesn’t mean simply training IT employees or those with access to sensitive systems. Every employee in your agency can be exposed
to phishing and social engineering and making them aware of the risks is an important activity. This is also something you can encourage your clients to do as well.
First step—have your employees complete Part 1 of this program.
Training begins with making employees aware of the risks—and security procedures—of clicking on bad websites and
links. Warn employees about scams and the dangers of clicking on unknown links in emails and texts.
There are a variety of programs—from free/inexpensive to security consultants with custom services—available.
Most
of the training centers around awareness-building.
The FBI has reported a 400 percent increase in cyber-attacks in 2020 – and, according to some reports, Ransomware makes up about 85 percent of those attacks.
Teach employees about the types of phishing attacks
Recognize specific phishing patterns and tactics
| Watering hole | Putting malicious code into a public website |
| Whaling attack | Uses social engineering to steal confidential information. The targets are usually big executives |
| Pretexting | Pretends to be someone else to get private information |
| Baiting | Malicious files often disguised as software updates |
| Quid pro quo | Offers a service or benefit in exchange for information or access |
What to watch for
- generic language, such as Mr. or Ms., Sir or Madame
- bad grammar, language or punctuation
- a sense of urgency
- requests for sensitive information, especially via email or text
Build understanding for things not to do
- don’t open emails from people you don’t know
- don’t click on links that aren’t safe—when in doubt hover over the link to see where it goes
- don’t just assume emails are ok
- don't assume that friends’ emails are automatically ok—they may already be infected
Fraudulent texting or smishing
Common attacks include:
- message from your bank, asking you to enter financial information
- trucking company or shipper asking you to schedule a delivery
- messages from other companies asking you to click links and enter information
What you should do—and not do
- don’t open links in text messages—ever
- check the sender’s address
- watch for misspellings and bad grammar
- contact the sender to see if messages are legit
Programs and information
There are a variety of training and information programs available.
- How to build a cybersecurity awareness program from Wizer: Comprehensive guide on how to build a successful Security Awareness Training Program
- Security Awareness Training for Employees and Certification Training Programs: Directory of the top cybersecurity education and training programs
- KnowBe4: Perform your own phishing tests and training on your timetable
- Cofense PhishMe: Phishing awareness training, anti-phishing training and threat simulations
- ProofPoint ThreatSim Phishing Simulations: Simulated attacks and knowledge and assessments
- Ransomware Readiness Assessment Tool: From the CISA—gauge your organization’s readiness and ability to defend against and recover from a ransomware attack
- PC360 Cybersecurity: Get informed by reading. Have employees check out these always-changing, up-to-date cybersecurity articles from P&C360
- SecurityIQ: Testing platform and awareness training
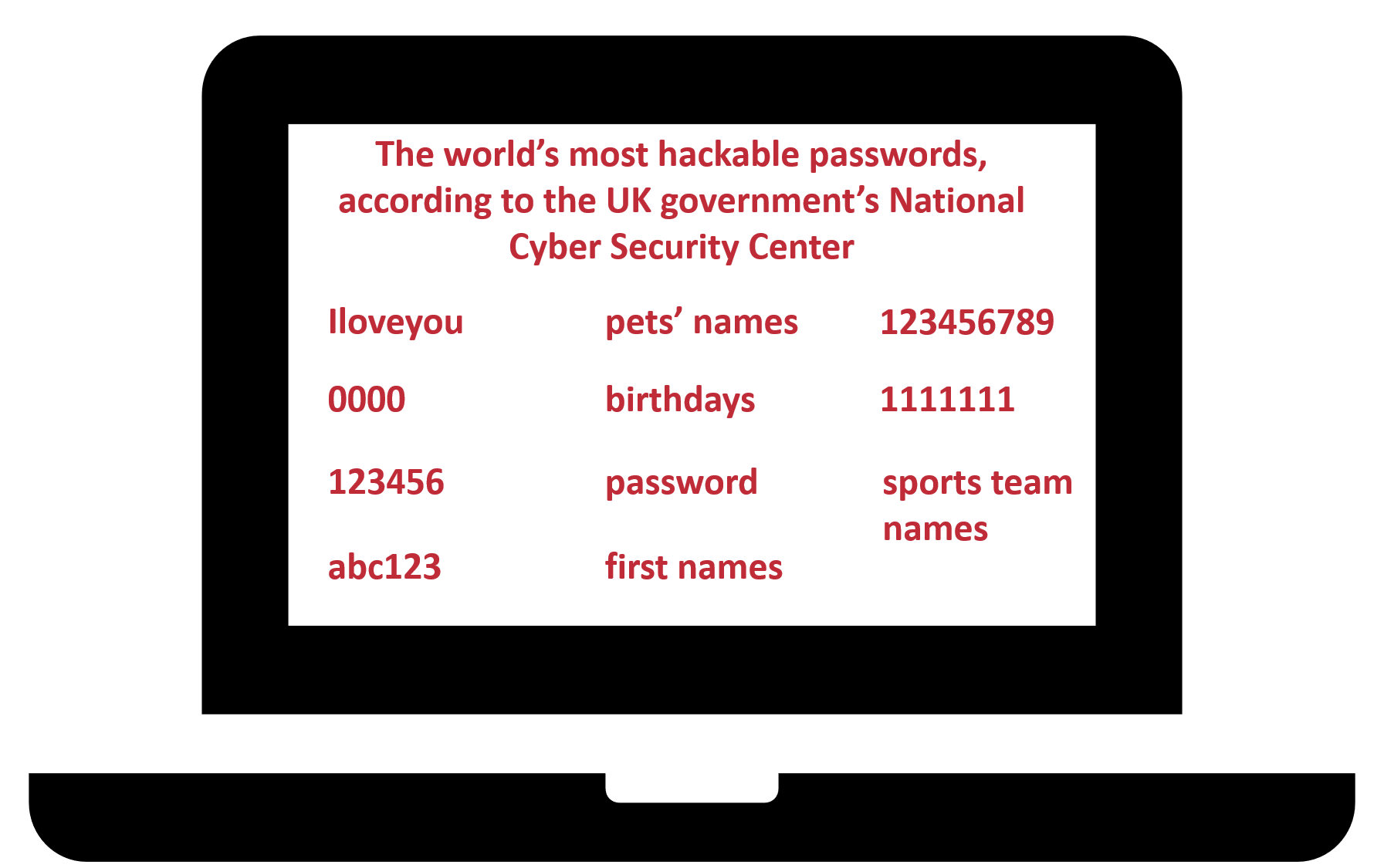
Passwords can be an important line of defense in your agency, but many principals have not spent time setting policies and working with your teams to show them good and bad examples.
Password management can be handled manually—by teaching your teams about password management. Or you can use a service to help manage passwords.
80 percent of cyber breaches are the direct result of stolen or hacked passwords (according to the 2017 Verizon Data Breach Investigations Report).
Password managers can help your team remember
You can organize your passwords manually and remember them or write them down and keep in a safe place (like a lockbox). You can also use a password manager which is a program that saves all your passwords in one location. It can also create complicated passwords and is accessed via a master password.
Additional resources:
1password--Paid password service that keeps online data safe
Bitwarden--Free password service that keeps online data safe
Read a review of the services in Wirecutter, The New York Times
It’s important to install antivirus protection on all electronic devices. This can be one of the most important technology solutions you have in battling cyberattacks. It’s important to select solutions you trust or that have been recommended to you. Make sure to run only one program though. If you run multiple programs, it can use unanticipated resources, but it can also result in less performance as the solutions may conflict.
New attacks targeting remote workers and business administration tools will likely be an issue throughout 2021, according to Security Magazine
You can also install antivirus applications on your smartphone and many of the major antivirus scanning brands also have phone applications.
Reviews and pricing for 10 antivirus solutions from US News and World Report.
The attack can be bad enough, but it’s important for agents to think about the recovery. These items should be on your checklist.
A significant number of breaches occur through third party vendors. These are called back-door attacks. It’s important to know that you can work with your vendors.
Here’s a checklist for opening the door to security discussions and monitoring your vendors
One of the key aspects of creating a more secure environment is to instill a security mindset within all employees. Follow this checklist to make your agency more secure.
- Communicate the negative impacts of a cyber incident on your business. Talk about potential losses with employees
- Discuss actual scenarios that have happened at other agencies and businesses
- Talk about what happens when you click on a bad link in an email or text, or visit a bad website
- Play a game ‘what would happen if’ someone texts you and asks for gift cards for the boss, a new employee asks for access to certain sensitive systems, someone guesses your password based on social media posts you’ve made. Make employees more aware of how their actions can impact the agency’s security
- Make cyber security everyone’s responsibility. Ask senior employees to help. Make a game of it—award prizes to those who show good judgment or who regularly pass tests
- Host regular cybersecurity sessions for employees. Discuss breaches they have heard about. Invite guest speakers. Make the meetings interesting and engaging
- Ask every employee to complete Part 1 of the PIA Partnership Winning@Cybersecurity Defense Program. Make sure they complete the quizzes to test their knowledge
- Implement phishing training programs to demonstrate how employees should be more careful
- Give employees a place to go to report suspicious links and to get questions answered
Advanced Toolkit
Many agencies outsource cybersecurity functions to a trusted security provider, working with a Managed Local Services Security Provider (MSSP) which offer information security monitoring and management. Many small and medium-sized business owners turn to managed security service providers (MSSPs) to help with their business’s threat prevention, continued IT processes, and quick recovery in the likelihood of an incident. They can also help identify and sort through security events.
Evaluating an MSSP: questions to ask
- What is the MSSP’s expertise and experience?
- What happens during the initial consultation?
- Describe the technical team—what is their experience and certifications?
- What types of services do you provide?
- What does the service cost?
- Does the MSSP tailor services to the agency or business?
- Do they create business continuity plans and incident response plans?
- Do they provide education on security for your team members?
- Is your MSSP’s location a good match for your agency or business (ie time zone)
- Have you spoken to other agencies or businesses using their services?
- What tools does it use?
- What is their own approach to security? Have they ever had a breach? What did they do?
- Do they outsource any of their services?
Difference between a Managed Services Provider (MSP) and a Managed Local Services Security Provider (MSSP)? A MSP focuses on usability and performance and an MSSP focuses on security. MSSPs often go deeper into security, including endpoint protection, multi-factor authentication and dark web monitoring.
Tasks your MSSP may perform
- security assessments
- threat assessments
- vendor assessment
- education
- software updates
- vulnerability scans
- password management
- multi-factor authentication
- network scans
- firewall development and reviews
One of the most important things you can do to increase online security is to enable multilevel authentication (MLA). This adds additional layers of security to password identification. With MLA you’re asked to enter one additional authentication method. You can do any number of ID methods for MLA—but most people do a minimum of two. Many insurers are starting to use MLA for access to their networks and applications.
Sending codes or passwords via email runs the risk of interceptions—which are on the rise
There are several types of authentication:
Laptops, mobile devices and security tokens
Answers to questions, passwords, PIN codes and randomly generated codes
Programs and Information
- New York Times Wirecutter review of Authy, 2-factor authentication service
- Authy - Free, available across platforms, and easy to use
- Gartner Group - Examples and ratings for a variety of vendors
There are a variety of emerging risks. We’re focused on a few here and will continue to add to this list.
Chat apps.
Pay attention to security in group chatting apps. Cisco’s threat intelligence unit warns about Discord and Slack as convenient ways to distribute malware.
QR codes.
Be careful about QR codes that—with the pandemic—have become more prevalent. Always verify the source. Some antivirus solutions have QR scanner apps you can use.
The Rise of Biometrics.
The introduction of biometric technology has been slow—but steady. Developers for mobile devices have been incorporating biometrics to enable users to bypass passwords. Biometric data is nearly impossible to phish, guess or hack. Forrester Research
predicts that in 2021 60 percent of global security decision-makers are planning to implement or expand their use of fingerprint,
facial or voice biometrics.
Discord and Slack.
Attackers are finding the file-sharing capabilities in popular group-chat apps such as Discord and Slack a convenient way to distribute malware, warns a new report from Cisco Talos, Cisco’s threat intelligence unit. The risk isn’t just that hackers can gain access to a particular channel and trick people in it into downloading malware. Once a file containing malicious code is uploaded, attackers can also grab a freely accessible link to that file where it’s hosted on the chat system’s servers. Then, they can send that link to people via phishing emails, misleading texts, or any other method they have of reaching potential victims.
Underwriters are looking at insureds’ security protocols and measures in increasing detail. Insurers making more and more specific IT security improvements a requirement before coverage can be bound. The report also says organizations must be mindful of new cyber regulations.
More information
Article: Discord and Slack are becoming a potent tool for malware attacks.
