Cyber Risk From A-Z
Cyber risk from A to Z: what you need to know about risks to your agency
We’ve designed this section to inform agents about the current cyber risks to your businesses. You and your team can take advantage of the materials, take the quizzes and then you can share with your clients to help them understand the potential impact on their businesses.
What it is
An unauthorized party issued instructions to your bank ordering the transfer of funds. This can happen in real life—by phone or fax—or it can happen online through email or online banking platforms. Or it can be a combination of both. Most frequently, a criminal has unauthorized access to your banking system by getting your credentials.
25% of businesses—large and small—are at risk
Risk stories
Marcy’s a bookkeeper for an insurance agency. She handles accounts payable and payroll, and the agency owner controls online banking and wire transfers. But while the owner is away, Marcy finds the banking passcodes under a mug on the owner’s desk and uses them to wire $5,000 to an offshore account.
Computer Virus
5 fast facts—what you need to know
- Over $800 trillion is moved via ACH (automated clearing house) or wire transfer. Both are considered a form of EFT (electronic funds transfer).
- 130 million EFTs take place each year.
- ACH is usually used for bill payment while wire transfers are typically just one-time transfers.
- An estimated $1.2 billion of the $800 trillion transferred electronically is tied to fraudulent activity.
- Fraudulent funds transfers are a federal offense similar to mail fraud.
Ways to decrease your risk
Train employees on proper security procedures and risks associated with clicking on unknown websites and links. Ensure employees are aware of how hackers can obtain unauthorized access, such as through:
- Malware from a tainted email or website
- Phishing (fake emails)
- Vishing (fake phone calls)
- Email compromise
- Stolen login credentials
Do not be careless with passwords
- Do not write them out or keep them on your computer or desk
- Do not open emails from accounts you do not recognize or seem suspicious
Install antivirus and anti-malware on all electronic devices
Install firewalls
Implement multi-level authentication and verification processes
Consider using a dedicated computer to do online banking (no emails or web)
Invest in ACH Debit Blocks or ACH Debit Filters
Take the Fraudulent Funds Transfer Quiz
What it is
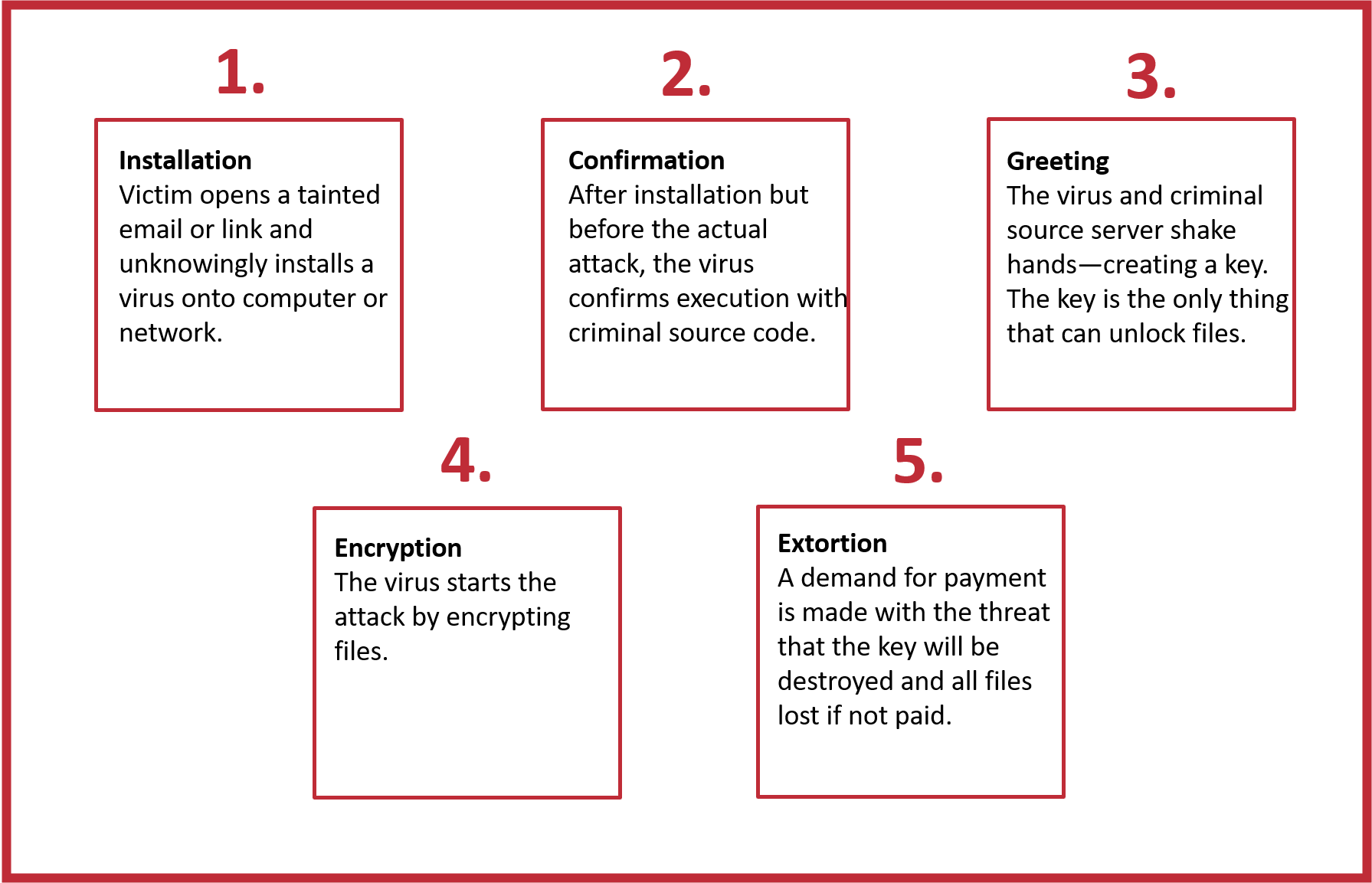
Ransomware is a global term for a type of computer virus that is used to hold your computer system or electronic data for ransom. Typical ransomware schemes will:
- Prevent you or your customers from accessing your computer systems
- Encrypt files to make them unusable
- Interfere with the operation of the computer or mobile applications.
In exchange for releasing your systems or data, the criminal asks for something in return.
More than half of small and mid-sized businesses don’t use data protection or email security, according to Intel Security
An agency was hit with a ransomware virus which locked its server and delivered an extortion demand for $1,000 in bitcoin. With its insurance carrier, the agency decided to pay the ransom as there were no backup files. The carrier helped acquire the bitcoin and settle the transaction. Once the criminals received the funds, the agency received the decryption code to restore its system.
5 fast facts—what you need to know
- Almost one-half of organizations have been hit with ransomware.
- The average ransom demand is just over $1,000.
- Email is the number one delivery vehicle for ransomware.
- Ransomware has grown 600% since 2015.
- Businesses and professional services are most frequently attacked.
Ways to decrease your risk
- Don’t open emails from people you don’t know
- Don’t visit unsafe websites
- Don’t click on malicious links in emails or social media posts
- Hacked computers should be disconnected from the WiFi and network immediately
- Make security everyone’s responsibility
- All incidents should be reported to the local FBI field office and the FBI’s Internet Crime Complaint Center
- Determine how the infection got in and close the hole
- Train employees to spot suspicious-looking emails or websites
- Implement strong password protection
- Communicate the impact that good security has on the agency’s business
- Backup systems frequently
- Have a business continuity plan and test it regularly
- Install, maintain and update antivirus software regularly
- Maintain application and operating system updates
- Have a communications strategy to keep clients informed
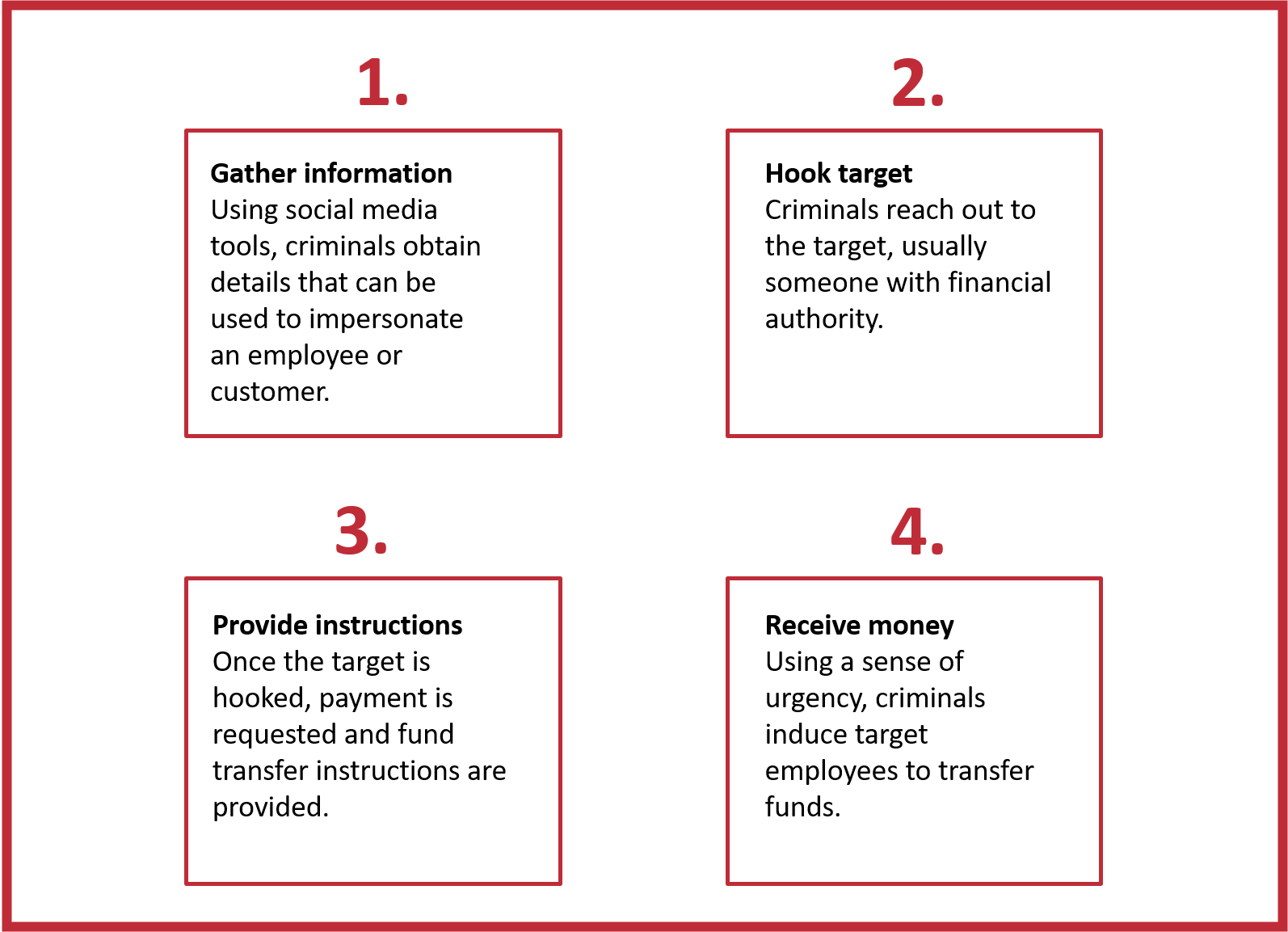
Social engineering is the practice of tricking an employee into revealing sensitive information or sending money to an unauthorized recipient. An email or phone call appearing to come from a legitimate business or individual can trick you into providing personal information. The scammers may also use social media to get personal information. Personal information is then used to impersonate a senior executive, vendor, or other person to trick the employee into sending money.
An email that looked like it came from the agency’s principal was sent to the agency’s CFO. It even contained specific, personal information about the CFO. It read: Before I forget, happy belated birthday. Good news, we just landed a great contract with a company here in Miami. They have agreed to supply us with the seals needed for our generators at a better rate than our current supplier. On my authority, please wire $20,000 to the following bank account. I’ll be back on Monday to discuss. The CFO followed the instructions and wired the money. When the principal returned to the agency, the CFO mentioned the new contract and the wire transfer and the principal says they never sent any such email.
Someone claiming to be a new client of the insurance agency called the account manager to cancel his employment practice's liability policy. The customer said he was having financial difficulties and needed to cut expenses. He requested that his refund be sent to a specific bank account ASAP because he wasn’t going to make payroll. The account manager wanted to help and agreed to send the funds immediately from the agency’s account. A day after the refund was issued, the actual client called to report an EPL claim. It became clear that there had been a fraud.
The agency’s accounting manager received an email that looked like it had been sent by the owner. It references how great her son’s team was doing in the baseball tournament. The email also instructed the manager to transfer $2,000 to the bank account listed in the email. The manager did as she was instructed, however it was soon discovered that the request was sent by an imposter.
4 stages of CEO fraud
7 fast facts—what you need to know
- It’s much easier to hack a person than a computer or network.
- Employees are busy, helpful and obedient—and make good targets.
- Emails are everywhere.
- The FBI estimates losses of close to $2.4 billion a year, including unreported activity.
- Organized crime is in the game, and a big part of the increase in attacks.
- The average loss for a company ranges from $25,000-$75,000.
- Top fraudulent email lines say payment, request and urgent.
Ways to decrease your risk
- Never provide confidential information via email, phone or text
- Be wary about people requesting payment through emails or phone calls
- Doublecheck email address and domain names
- Verify sources using other channels (such as phone) before complying. Never rely on email alone
- Don’t let the urgency in senders’ messages sway your judgment
- Review your website and social media to ensure that travel and other plans aren’t disclosed
- Maintain a security-aware culture. Educate employees at all levels of the agency
- Don’t deviate from controls that have been put in place—even if it’s the CEO who is asking
Cyber business interruption (CBI) is an operational business failure due to a cyberattack, or non-physical event.
The agency’s website provider was hit in a Denial of Services attack. The provider could not quickly resolve the attack to its systems and the agency’s website was taken offline for four days while the problem was fixed. The agency incurred financial loss due to lost income and reputational damage.
Cyber criminals used malicious code to sabotage the agency’s automated building controls. The code turned off the cooling systems which, in turn, meant the employees could not go to work.
5 fast facts—what you need to know
- Cyber incidents that cause business interruption have been increasing.
- Small and mid-sized businesses lose an average of $100,000 from CBI.
- The most common CBI events are due to network and website disruptions.
- Nearly one quarter of the losses are from businesses with less than $10M in revenue.
- Top industries impacted are IT, public administration, finance, insurance and service.
Ways to decrease your risk
- Keep your environment secure—use antivirus software and ensure firewalls and routers are secure and up-to-date
- Back up data and systems regularly
- Accept software upgrades and patches
- Use strict password policies
- Educate employees
- Create an incident response plan
What it is
A data breach is an incident in which information is stolen or taken without the owner's knowledge or permission. If the stolen information includes the names and medical or financial records of individual people, in most states, the information’s owner has obligations under the law to address the breach and notify the impacted individuals.
While moving offices, an employee threw away a box of HR files. The company later learned that the entire box – three years’ worth of employment records – were pulled out of the garbage by an unknown person.
Hackers—backed by a professional criminal organization--steal credit card information from the agency’s customers. Financial data was used to purchase electronics and small luxury goods around the world. The company’s insurance company’s incident response expert guided the agency's response in issuing notifications and providing credit monitoring and identity theft services for its customers. Despite their best mitigation efforts, the customers brought a class action suit against the agency for failure to protect private data.
7 fast facts—what you need to know
- All 50 states have data breach notification laws.
- Federal laws govern healthcare information (HIPAA). Under HIPAA, covered entities and individual executives or employees face criminal liability for knowingly obtaining or disclosing protected health information.
- A new federal law has been proposed—the Data Security and Breach Notification Act--would require organizations to notify individuals within 30 days of a breach, among other things.
- Breaches are expensive, costing an average of $141 per record to rectify.
- Overall, 61% of breaches hit smaller businesses.
- It’s not just the hackers you have to worry about—system glitches and human error can cause disclosure of private data.
- A majority—60%--of small businesses go out of business within six months of an attack.
Ways to decrease your risk
- Set up an incident response team
- Make extensive use of encryption
- Conduct employee training
- Use security analytics
- Appoint a Chief Information Security Officer
- Engage your Board of Directors or other leadership in security and risk management
Network security maintains the integrity of your computer systems, network and data. A good network security platform will restrict access to your network, prevent malware from entering your system, and keep malware from spreading through your system. Network security includes access control, antivirus, application security, email security, behavioral analytics, firewalls, VPNs and web and wire security.
The agency faced a virus that wiped out hard drive after hard drive. It eventually became obvious and backups were made. No virus scanners could locate it or remove it. The agency had to replace all computers as well as everything with a USB port. All files were thrown out and the agency had to start from scratch.
The agency’s potential clients were making appointments on the company website. Yet they were getting an email from an outside company pretending to be a representative of the agency. The fraudster induced the clients into providing sensitive information.
2 fast facts—what you need to know
- Cyber Crime is a thing—damages will cost the world $6 trillion annually this year, making it more profitable than the global trade of all major illegal drugs combined.
- More than 40% of cyberattacks are on small businesses with fewer than 250 employees.
Ways to decrease your risk
- Restrict access to your network
- Install antivirus software
- Utilize firewalls and VPNs
- Require employees to have strong passwords (utilizing numbers, upper and lowercase, and special characters)
- Prohibit employees from connecting personal mobile devices to network (such as smartphones)
What it is
Website media liability includes a variety of publishing acts, including defamation; libel; slander; disparagement; invasion of privacy; plagiarism, copyright infringement; and some forms of advertising injury for all of the material distributed on company websites and social media accounts.
An agent on their lunch break used their work computer to post a negative opinion about a previous agency they worked for. Because of the way the posting platform was setup, the post was linked to the poster’s current agency. The agent’s former employer sued the agent’s new agency for defamation.
An agency wants to update its website to include stunning visuals. One of its employees said they have experience designing websites and offers to help. The employee searches for images online and pulls the ones they like – without checking about copyright or usage permissions. Once the website with the new images is live, the agency receives a notice informing them that the owner of one of the photos used on the updated website is suing them for copyright infringement.
3 fast facts—what you need to know
- The internet is becoming the largest medium for advertising and 75% of small business owners see internet marketing as an effective tool to attract new customers.
- Overall 71% of small businesses do their own digital marketing.
- More than half of companies have no system in place to monitor employee use of social networking sites and only 10% have social networking policies.
Ways to decrease your risk
- Monitor your online presence and understand how your business is being portrayed online
- Decide which type of statements require a company response
- Have a written policy that covers all forms of electronic communication
- Decide which employees have authority to publish on social media or add website material
- Conduct periodic reviews of your website and other published material
- Train employees on the risks of using social media for the company and as individuals
